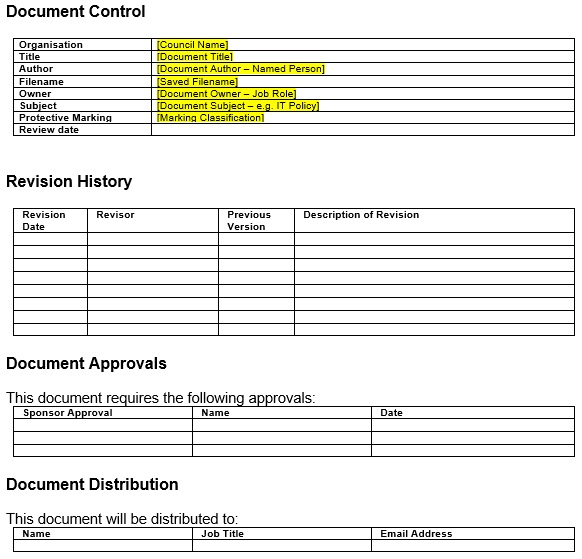
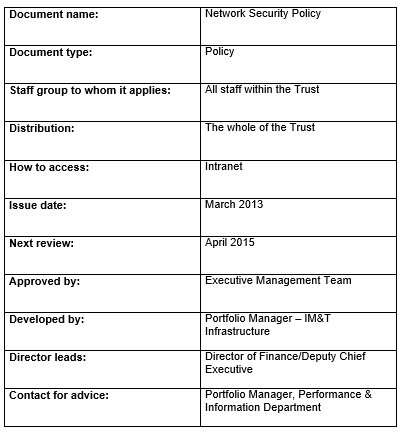
An information security policy template is a single document or set of documents relevant to each other. A security policy includes a description of the security controls and it rules regarding the activities, systems, and behaviors of an organization. Instead of describing specific solutions to problems, this document define the conditions that will help protect the assets of the company.
Furthermore, an information security policy should address the following concerns;
- The prevention of wastes
- The unsuitable use of the resources of the organization
- Removal of potential legal liabilities
- The safety of the valuable information of the organization
Table of Contents
- 1 What is an information security policy?
- 2 Types of security policy templates:
- 3 What should a security policy template include?
- 4 The purpose of an information security policy:
- 5 How to create your security policy template?
- 6 What is the significance of an information security policy?
- 7 Steps to follow to get benefit from using a security policy template:
- 8 Conclusion:
- 9 Frequently Asked Questions (FAQs)
What is an information security policy?
An information security policy is a document used by an organization to design a set of rules, policies and procedures. These policies make sure the IT security and data protection security requirements. Aside from IT security and physical security, the security policy also covers social media usage, lifecycle management and security training.
Types of security policy templates:
A security policy provides the protection of information that is related to the company. It doesn’t matter what the nature of your company, several security issues may occur. These issues may come from different factors including improper sharing and transferring of data. You should create foolproof security policies in order to keep your company protected. There are different types of security policy templates that you can make;
Information security
This will give policies regarding the protection of schools and their stakeholders. The high authorities of the school develop the policies. They make rules to safeguard the most valuable information and assets of the school.
Data security
This will speak about the policies that will safeguard data on computers and servers. It would explain computer and password security and deal with data backup, internet and email usage, and more.
Network security
This type of security policy speak about specific policies. They would pay attention on protecting the integrity, confidentiality, and accessibility of the network. It will also explain the accountability of the network’s security. The template may contain the risk assessment of the components of the network.
Physical security
This would give policies that will safeguard assets and resources from damages. It can assist in developing and documenting all potential security risks. At a lower cost, the template can also give the execution of safeguarding from risks.
Corporate security
This template is used to make sure the protection of assets, persons, and company capital.
What should a security policy template include?
A security policy would include the policies whose main purpose is to secure a company’s interests. For example, you can use a cybersecurity policy template in order to safeguard all your software, hardware, network, and more. It contains everything that is related to the company that’s relevant to the cyber aspect.
However, a security policy template should include the following relevant information regarding your company’s security policies;
- Guidelines on how to store transmit or share information safely.
- The policies that are relevant to the use of devices, machines, and equipment. When using these things, the employees of the company should follow these policies.
- The policies regarding the use of the company’s network and wireless network.
- The policies about the usage of sensitive software. This will protect any threats of viruses and malware.
- The policies regarding monitoring the security.
- The details about the authority to block any devices that include security breaches.
- Details about the implementation of policies that are more cost-effective.
A security policy is used by different kinds of organizations. It’s useful in protecting the interests of the company that contains resources and assets.
The purpose of an information security policy:
The main purpose of this document is to provide protection and limit the distribution of data to only those who have authorized access. Let us discuss below some other reasons of drafting this document;
- The organizations or companies draft it to have a general approach to information security.
- This document contains security measures as well as policies regarding the user access control.
- They use it to analyze and reduce the impact of compromised information assets like misuse of data, networks, mobile devices, and more.
- It safeguards the reputation of the organization.
- Companies make information security to secure their customer’s data like credit card numbers, etc.
- It provides an effective way to react to complaints and queries relevant to real or perceived cyber security risks.
- People who are using an acceptable key information technology assets, you can use it to limit their access.
How to create your security policy template?
Here are some pointers to help you in creating a security policy;
- May be this is your first time to creating such type of document. You should also undergo the process of risk assessment while developing your policies. In this process, you have to first develop all the potential risk sources.
After that, start thinking of policies to reduce, transfer or remove those risks. In your company, you also have to apply these to all the employees. All the employees from lowest to the highest should know how to deal with these risks. - Identify the scope of your security policy template. You should determine whether it apply to the whole company or just a department. Then, create your policies accordingly.
- Creating your security policy involves different activities. You just have to sit down with a team and start thinking of the instructions. You have to brainstorm ideas after risk assessment. Make a strategy to overcome all these potential risks. You must do this so that you don’t place any aspect of your company in danger.
- Next, you have to develop the roles of employees in the security policies. You should determine that which employees have the bigger responsibilities in terms of safeguarding the assets and interests of the company. You may generally select the IT or technical support staff and other employees. All these people can play a significant role in securing your company well.
- You should ensure to evaluate your current activity before finalizing your policies. Moreover, for security based on your hardware and equipment, assess the minimum requirements.
This will assist you in developing the suitable security level to set for your company. For example, you have to secure all the computers for your employees. You can set policies such as modifying passwords every month. - You can try executing the policies after you have defined them. Before finalizing your document, do this and see if they work. You have to execute the policies well by explaining them to your employees clearly. This will help the employees in understanding better. You can also motivate your employees to ask questions regarding anything that’s unclear.
- You have to monitor the progress of your company when the policies are already in place. You have to ensure that there are improvements in the security rather than weaknesses. Additionally, you should also keep them updated.
What is the significance of an information security policy?
In preventing security incidents, a critical step is to make an effective security policy that fulfills all compliance requirements. For new and established organizations, ISPs are of great importance. When you enhance digitalization, it indicates that every employee is generating data. A section of that data must be secured from unauthorized access. Even, it may be secured by laws and regulations, however, it is based on your industry.
At every level of your organization, you require information security policy because it provides protections to sensitive data, PII (Personal Identifiable Information), and intellectual property.
Steps to follow to get benefit from using a security policy template:
You can get an extreme benefit from using security policy template. You should follow the below steps in case you get benefit from this template;
Select the right template
It’s up to you whether you may make your own template or you may download it online. You just have to make sure that you have selected the right one. Your security policy template should be comprehensive containing all the necessary information without being too complex. Neither make it too simple nor too complicated because your readers can’t understand and comply with it.
In case, you have downloaded a template so it may not fit into your own company’s requirements so you must make modifications to it before releasing it to the employees. Also, you can consult with a professional if you aren’t sure about your template. Furthermore, when it comes to security policies, you must learn about the requirements of jurisdictions because different jurisdictions may have different requirements.
Your template must comply with the applicable law of your state. It is advisable to consult with a security professional in order to make things easier.
Make adjustments to your template as per your company’s requirements
After downloading or making your template, you should keep on making adjustments in order to make your template according to your company’s requirements and location. An information security officer of your company should establish this document because he better knows the standards of security policies and the applicable laws.
In addition, you must know the language which is used to write the security policies as well as the drafting styling that is applied to the template. These documents are generally written by using complex legal terminology. These terminologies should be used in such a way so that it would be easily understand by your employees.
Your employees will easy understand the policies and follow them in case they are clear, concise, and easy to understand. Always keep your template updated and applicable.
Make sure that every member of your organization comply with everything written on your document
To save time and effort, most of the companies download templates from internet and modify them to suit their own needs. This way, they can’t get benefit from this security policy. When you have done with your document, you have to release it to your employees and after sometime ask them whether they understand everything written on it or not.
In order to make sure the effectiveness of your document, you should note that whether the security of your company has enhanced due to these policies. In case, you don’t observe any positive changes then you may have to modify your document.
Conclusion:
An information security policy template is an extremely beneficial document that protect the privacy of the company. This document allows the restriction of employees from performing inappropriate actions. In the document, you can establish policies regarding password security, digital signatures, and so much more.
Frequently Asked Questions (FAQs)
There are 5 major elements of ISPs;
1- Confidentiality
2- Integrity
3- Availability
4- Authenticity
5- Non-repudiation
It refers to the following;
1- Acceptable use policy (AUP)
2- Access control policy (ACP)
3-Change management policy
4- Information security policy
5- Remote access policy
6- Email/communication policy
7- IT operations and administration policy
8- Data security policy
9- Identity access and management (IAM) policy
10- Personal and mobile devices policy